
In order to prevent successful cyberattacks, many organizations collect indicators of compromise (IOCs) from various threat intelligence providers with the intent of creating new controls for their security devices. Unfortunately, legacy approaches to aggregation and enforcement are highly manual in nature, often creating complex workflows and extending the time needed to identify and validate which IOCs should be blocked.
Now security organizations can leverage MineMeld, an open-source application that streamlines the aggregation, enforcement and sharing of threat intelligence. MineMeld is available for all users directly on GitHub, as well as pre-built virtual machines (VMs) for easy deployment. With an extensible modular architecture, anyone can add to the MineMeld functionality by contributing code to the open-source repository.
MineMeld use cases
MineMeld supports a variety of use cases, with more being added each day by the community, including:
- Aggregation and correlation of threat intelligence feeds
- Enforcement of new prevention controls, including IP blacklists.
- Evaluate the value of a specific threat intelligence feed for your environment.
- Extract indicators from Palo Alto Networks device logs and share them with other security tools.
- Share indicators with trusted peers.
- Identify incoming sessions from Tor exit nodes for blocking or strict inspection.
- Track Office365 URLs and IPs
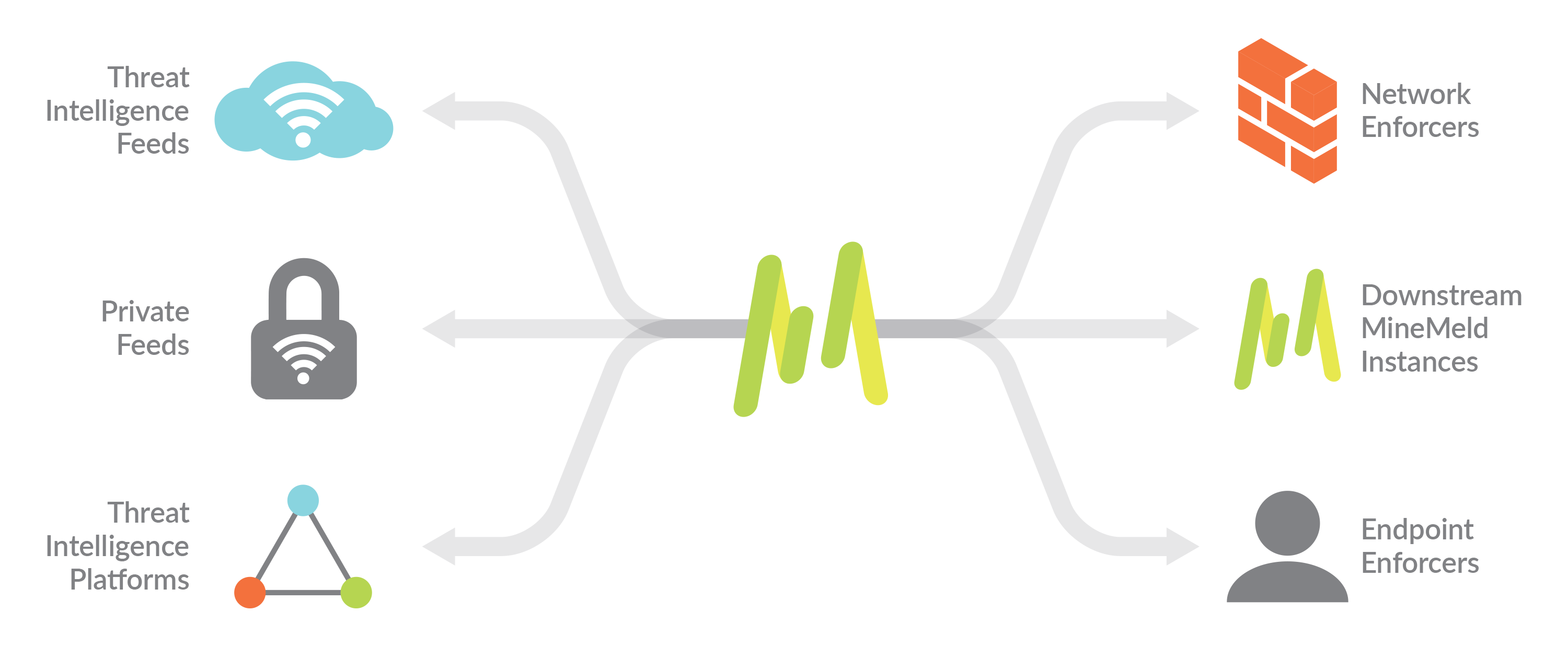
Aggregate and correlate threat intelligence feeds
MineMeld allows you to aggregate threat intelligence across public, private and commercial intelligence sources, including between government and commercial organizations.
MineMeld simplifies the collection and correlation of intelligence across:
- Commercial threat intelligence feeds
- Open-source intelligence (OSINT) providers
- Threat intelligence platforms
- ISACs
- CERTs
- Other MineMeld users
Once indicators are collected, MineMeld can filter, unduplicate and consolidate metadata across all sources, allowing security teams to analyze a more actionable set of data, enriched from multiple sources, for easier enforcement.
Automated enforcement of prevention-based controls
MineMeld natively integrates with Palo Alto Networks security platforms to automatically create new prevention-based controls for URLs, IPs and domain intelligence derived from all sources feeding into the tool. Now, organizations can simplify their workflows for blocking IOCs with External Dynamic Lists and Dynamic Address Groups, without spending additional resources to manage block lists, including the automated timeout of expired indicators. MineMeld further integrates with the Palo Alto Networks AutoFocus™ contextual threat intelligence service, allowing you to identify high-value, targeted indictors – in AutoFocus – and block them on your next-generation firewall with export lists and MineMeld.
Threat-intelligence-sharing ecosystem
Palo Alto Networks has partnered with other leading organizations to create a threat-intelligence-sharing ecosystem with native MineMeld support built in from the start. Additionally, the open-source availability inherent in MineMeld allows other providers to easily add integration with their offerings by building a new Miner.
Availability
MineMeld is publicly available to customers, partners and the security community as an open-source tool. You can get started using MineMeld by visiting:











